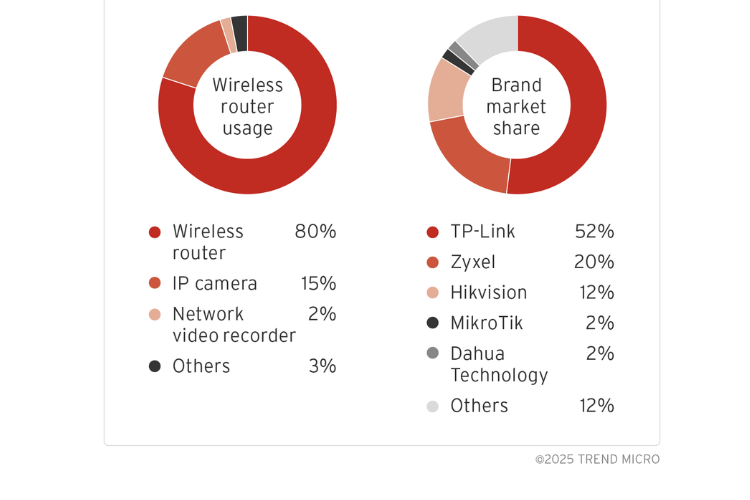
A newly discovered Internet of Things (IoT) botnet has been carrying out large-scale Distributed Denial-of-Service (DDoS) attacks across the globe. Since the end of 2024, this botnet has targeted networks and servers, overwhelming them and causing major disruptions. The botnet exploits weaknesses in IoT devices such as routers and IP cameras, which are widely used in homes and businesses. The malware used by the botnet is mostly derived from the Mirai and Bashlite families which are well-known for exploiting vulnerabilities in connected devices. The majority of infected devices are wireless routers, accounting for 80% of the compromised units. Around 15% of infected devices are IP cameras. These devices are from well-known brands such as TP-Link, Zyxel and Hikvision.
The botnet malware gains access to IoT devices by either exploiting Remote Code Execution (RCE) vulnerabilities or taking advantage of weak default passwords, which are often left unchanged by users. Once a device is compromised, it downloads additional malicious payloads and connects to a central command-and-control (C&C) server to receive attack instructions. The malware utilizes various DDoS techniques including SYN Floods, UDP Floods and GRE Protocol Exploits. These attacks flood networks and servers with excessive traffic, causing them to become unresponsive or even crash. As a result, businesses and organizations across different sectors have experienced interruptions in their operations.
While the botnet is affecting global targets, there are noticeable regional differences in the attack patterns. The sectors most impacted in by this attack includes telecommunication, information technology and cloud computing. Furthermore, Japanese organizations have been subjected to attack strategies that are different from those used in other regions with commands like “stomp” appearing more frequently in attacks against Japan.
Experts in cybersecurity are concerned about the growing threat posed by weak IoT device security. Many devices still use unchanged default passwords or run outdated firmware, leaving them vulnerable to attacks. To protect against such threats, experts recommend taking immediate action. This includes isolating IoT devices on separate networks, changing default credentials and using Intrusion Detection Systems (IDS) to detect unusual traffic patterns. The rise of IoT-based DDoS attacks highlights the urgent need for improved security measures. Organizations and individuals must take proactive steps to secure their IoT devices to prevent becoming targets in the next wave of cyberattacks.